Web Parameter Tampering attack
The Web Parameter Tampering attack is based on the manipulation of parameters exchanged between client and server in order to modify application data, such as user credentials and permissions, price and quantity of products, etc. Usually, this information is stored in cookies, hidden form fields, or URL Query Strings, and is used to increase application functionality and control.
This attack can be performed by a malicious user who wants to exploit the application for their own benefit, or an attacker who wishes to attack a third-person using a Man-in-the-middle attack. In both cases, tools likes Webscarab and Paros proxy are mostly used.
The attack success depends on integrity and logic validation mechanism errors, and its exploitation can result in other consequences including XSS, SQL Injection, file inclusion, and path disclosure attacks.
Impact : Cost Impact on purchasing the products online .
How it can done:
1. look for the vulnerable website where there is data tampering is possible
2.Configure the Burp proxy to intercept the traffic between client and server
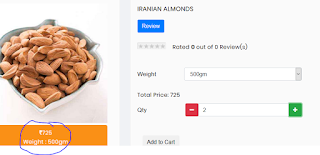
3.i have choose something as below screen shot which cost 750*2=1500
4.I know price parameter is vulnerable so i manipulated i changed to 1 Rupee only i selected quantity as 2 so i get the selected product only for 2 Rupees
5. Then i have forwarded the request with manipulated parameter , booom that was reflected in response and able to see the changes .
Happy Hacking :-)