Are You worried about roaming users? - Enterprise Security
Using the Zscaler App, users can get all of the benefits of the Zscaler service for Internet traffic, as well as granular, policy-based access to internal resources from a single point.
Ø With the app's Internet Security feature, you can protect your users' web traffic even when they are outside your corporate network. The app forwards user traffic to the Zscaler service and ensures that your organization's security and access policies are enforced wherever they might be accessing the Internet.
Ø With Zscaler Private Access (ZPA), you can enable your users to securely access enterprise applications from outside the corporate network. ZPA establishes a secure transport for accessing your enterprise apps and services.
Ø Zscaler App will enable us to enhance the endpoint security of road warriors, mobile users with enhanced control and visibility
Installation Procedure of Z-App :
Ø Download the latest version of application for suitable OS (windows, Mac)

Ø Sign with the credentials your organization domain ID.
Example: exaple@org.com
> Please select “Zscaler” as Cloud , depends on your organization selected
Ø Accept the “domain” sign in policy.
Ø Automatically your device will be provisioned once you accept the “Org ” Policies.
Ø Done with registration of device and Installation of Z-App in Desktop.
Z-App Cloud Console Administration Configurations:
Below is the Screenshot of Z-App Administration Tab.
Ø Zscaler app store is to know the latest update versions and current update settings:
Ø Zscaler App notification Tab used to configure Notification message appears at when user or
Admin try to provision new device. [<b> text to show </b>]
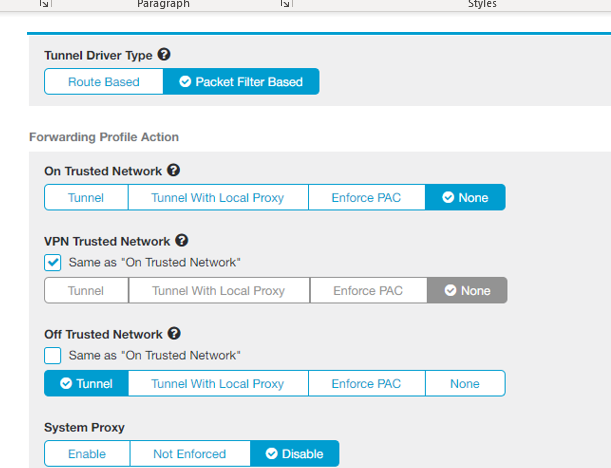
Forwarding Profile :
Ø Forwarding profile is used to identify the Zscaler App to identify the traffic to where to forward via Tunnel.
Ø One organization can have multiple forwarding profiles to different Users to different destinations as per company requirements.
Example:
While forwarding the profile to Zscaler App we taking consideration DNS entries, VPN tunnel IP-address, and DNS search domains as below .
Forward Profile name
|
DNS –Server names/IP-address
|
DNS-search names
|
Laptop
|
List of your internal Domain IP's to identify the traffic to choose forward profile
|
example1.com
example.2com
|
Network Identification criteria:
1. Trusted network:
Ø User is inside the corporate network.
2. VPN Trusted network:
Ø User is outside network and connected via cisco client VPN.
3. Off-Trusted network:
Ø User is outside the corporate network using any other external network
Note: As per our current configuration Zscaler app work status will active only on “off-trusted “network as above.
We can modify the working procedure of Zapp configuration accordingly as per requirement.
Ø Current Zscaler App configured to off-trusted network functionality with PAC file enforcement for specific URL’s Bypass methodology.
Ø That PAC file will be configured in forwarding profile when traffic is identify by Zscaler App then fetch conditions from Custom PAC configuration and redirect the users accordingly.
Ø You can see this PAC file configuration in below location.
Zscaler Admin portal -> Administration->Hosted PAC file.
Here is the sample configuration for PAC file:
App-Profile:
Ø Zscaler app profile used for user to restrict web-traffic based on policy configured for that forwarded profile.
Ø When user network is identified in forwarded profile, Zscaler App looks for the app profile download and work accordingly configured rules for that app profile.
ZApp Road Worries Policy :
Accorrding to your wish you can configure the policies for URL & Application category .
Basic Policy recommended as below.
Note : (Mobile Security is also possible tuning the forwarding profile configuaration)